[eBook] The PFAS Handbook: The Ultimate Guide to Identifying & Mitigating PFAS Risks in Your Supply Chain – Download Now
Clear Visibility
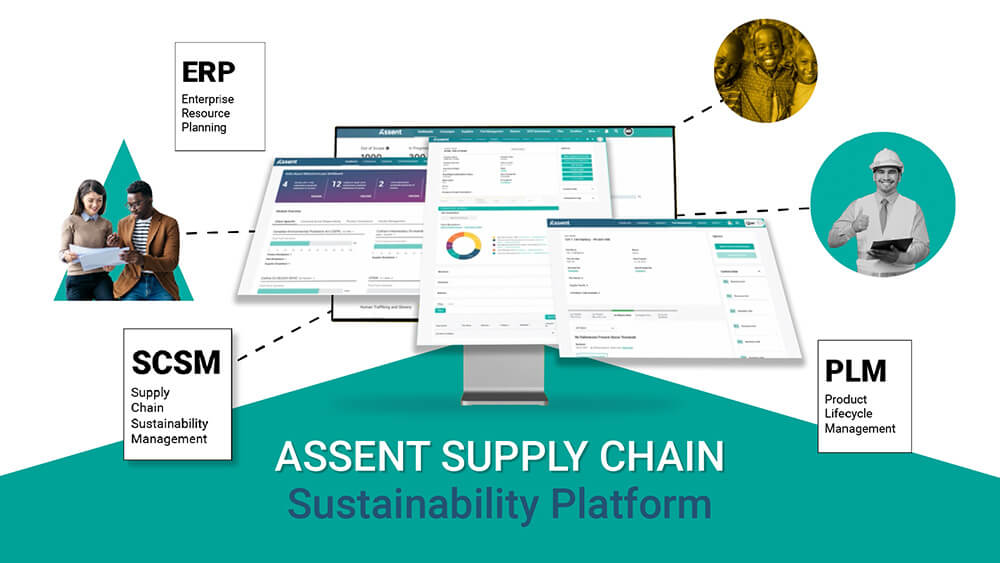
Into Supply Chain Risk
Empowering global manufacturers with solutions for
Helping Complex Manufacturers Lead the Way
in Supply Chain Sustainability Management
Join a community committed to setting new standards in compliance and ESG.




























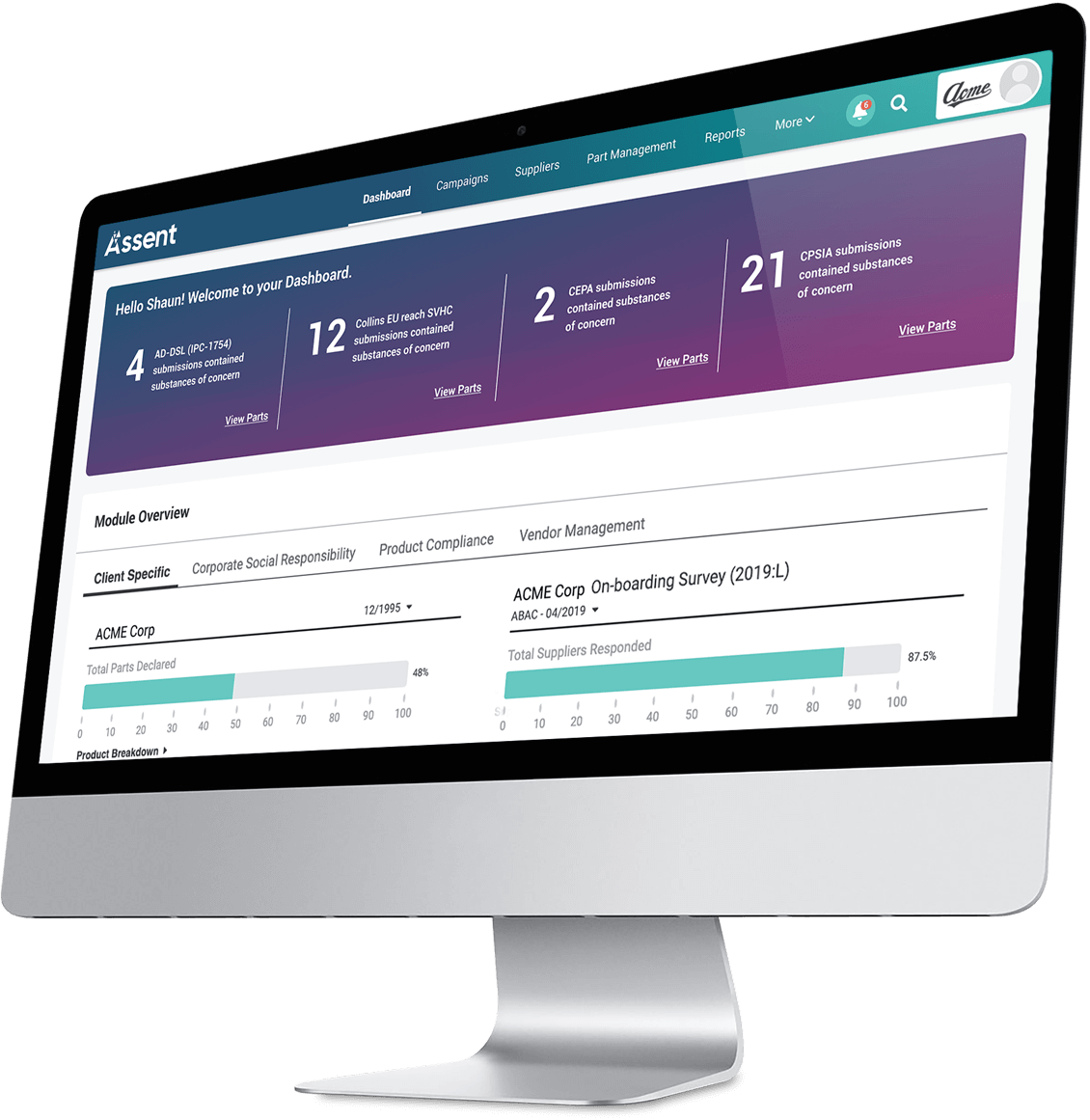
Discover Our Featured Solutions & Highlights
304% ROI Over Three Years
According to a commissioned Forrester Consulting Total Economic Impact™ Study, manufacturers that invested in the Assent platform experienced 304% ROI over three years through improved supplier engagement and reduced non-compliance costs.
Download the Study“Assent is probably saving us millions of dollars in fines alone, ignoring any other legal implications of compliance violations.”
— Head of supplier regulatory compliance, home appliances.